Evaluación de aptitudes prácticas
TODO SOBRE CCNA v7 – CISCO
Evaluación de aptitudes prácticas PT de SRWE (PTSA) - Parte 1
CCNAv7: Switching, Routing e Wireless Essentials v7.0 (SRWE)
SRWE PT Practice Skills Assessment (PTSA) Parte 1
Tipo 1 – 192.168
Algunas cosas a tener en cuenta al completar esta actividad:
- 1. No utilice el botón Atrás del navegador ni cierre ni vuelva a cargar ninguna ventana de examen durante el examen.
- 2. No cierre Packet Tracer cuando haya terminado. Se cerrará automáticamente.
- 3. Haga clic en el botón Enviar evaluación en la ventana del navegador para enviar su trabajo.
Introducción
En esta evaluación, está configurando una red que utiliza EtherChannel y enrutamiento entre VLAN. En aras del tiempo, no se le pedirá que realice todas las configuraciones en todos los dispositivos de red, como se le puede solicitar que haga en una red real u otra evaluación. En su lugar, utilizará las habilidades y los conocimientos que ha aprendido en las prácticas de laboratorio de este curso para configurar el enrutador y los conmutadores en la topología. Además del enrutamiento EtherChannel y entre VLAN, esta tarea implica la creación de VLAN y troncales, y la configuración básica de enrutadores y conmutadores.
Debe configurar las puertas de enlace predeterminadas del host; sin embargo, las direcciones de host están preconfiguradas.
Practicarás y serás evaluado en las siguientes habilidades:
- Configuración de los ajustes iniciales en un enrutador.
- Configuración de los ajustes iniciales en un conmutador, incluidos SVI y SSH.
- Configuración de VLAN.
- Configuración de la membresía de VLAN de switchport.
- Configuración EtherChannel.
- Solución de problemas de VLAN.
- Configuración de enlaces estáticos y DTP.
- Configuración de enrutamiento entre VLAN en un conmutador de capa 3.
- Configuración del enrutamiento entre VLAN enrutador en un dispositivo móvil en un enrutador.
- Configure las puertas de enlace predeterminadas en los hosts.
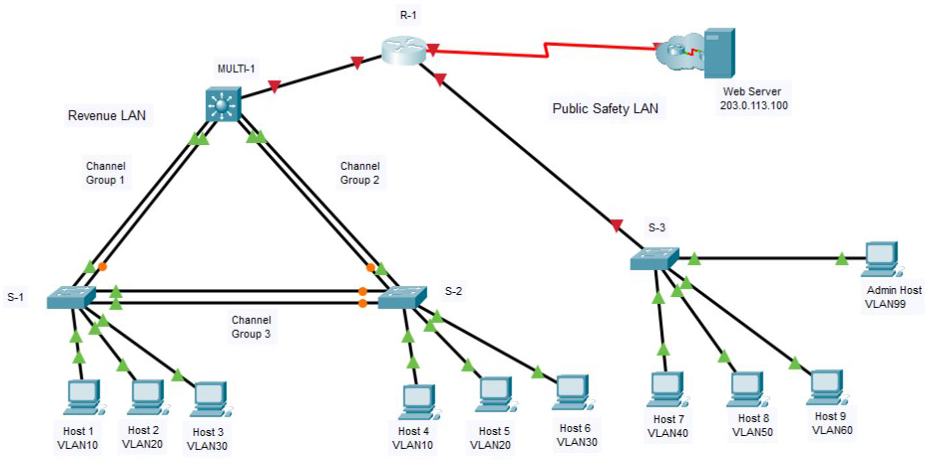
Tabla de direcciones
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| R-1 | G0/0/0 | 192.168.0.1 | 255.255.255.0 |
| G0/0/1.40 | 192.168.40.1 | 255.255.255.0 | |
| G0/0/1.50 | 192.168.50.1 | 255.255.255.0 | |
| G0/0/1.60 | 192.168.60.1 | 255.255.255.0 | |
| G0/0/1.99 | 192.168.99.17 | 255.255.255.240 | |
| S0/1/0 | 209.165.201.2 | 255.255.255.252 | |
| MULTI-1 | G1/1/1 | 192.168.0.2 | 255.255.255.0 |
| VLAN10 | 192.168.10.1 | 255.255.255.0 | |
| VLAN20 | 192.168.20.1 | 255.255.255.0 | |
| VLAN30 | 192.168.30.1 | 255.255.255.0 | |
| VLAN99 | 192.168.99.2 | 255.255.255.240 | |
| S-3 | VLAN99 | 192.168.99.18 | 255.255.255.240 |
| Host 1 | NIC | 192.168.10.10 | 255.255.255.0 |
| Host 2 | NIC | 192.168.20.20 | 255.255.255.0 |
| Host 3 | NIC | 192.168.30.30 | 255.255.255.0 |
| Host 4 | NIC | 192.168.10.11 | 255.255.255.0 |
| Host 5 | NIC | 192.168.20.21 | 255.255.255.0 |
| Host 6 | NIC | 192.168.30.31 | 255.255.255.0 |
| Host 7 | NIC | 192.168.40.40 | 255.255.255.0 |
| Host 8 | NIC | 192.168.50.50 | 255.255.255.0 |
| Host 9 | NIC | 192.168.60.60 | 255.255.255.0 |
| Admin Host | NIC | 192.168.99.19 | 255.255.255.0 |
| Wed Server | NIC | 203.0.113.100 | 255.255.255.0 |
Antecedentes / Escenario
Una corporación planea implementar EtherChannel y un nuevo diseño de VLAN para hacer que la red sea más eficiente. Se le ha pedido que trabaje en un diseño y prototipo de la nueva red. Ha creado la topología lógica y ahora necesita configurar los dispositivos para evaluar el diseño. Configurará las VLAN y la membresía de VLAN del puerto de acceso en los conmutadores de la capa de acceso. También configurará EtherChannel y trunking. Finalmente, configurará un enrutador y un conmutador de Capa 3 para enrutar entre VLAN. Ya se habían configurado algunas direcciones.
Instrucciones
Parte 1: Configuración básica del enrutador
Paso 1: Configure el enrutador R-1 con los ajustes necesarios.
una. Abra una ventana de comando en el enrutador R-1 y pase al modo EXEC privilegiado
b. Copie y pegue la siguiente configuración en la CLI del enrutador R-1.
Router(config)#ip route 192.168.10.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 192.168.20.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 192.168.30.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 192.168.99.0 255.255.255.240 GigabitEthernet0/0/0
Asegúrese de presionar la tecla Enter después de la última línea para volver al indicador del modo EXEC privilegiado.
C. Configure los siguientes ajustes en el enrutador
: la contraseña secreta de habilitación.
– Una contraseña de consola
– Acceso remoto a las líneas VTY.
– Un mensaje de banner MOTD.
– El nombre de host del dispositivo según el valor en la tabla de direccionamiento.
– Todas las contraseñas de texto sin cifrar deben estar cifradas.
– Direccionamiento de interfaz en g0 / 0/0 y s0 / 1/0
– Descripciones de interfaz en g0 / 0/0 y s0 / 1/0.
Router(config)#no ip domain lookup Router(config)#enable secret class Router(config)#line console 0 Router(config-line)#password cisco Router(config-line)#login Router(config-line)#exit Router(config)#line vty 0 4 Router(config-line)#password cisco Router(config-line)#login Router(config-line)#exit Router(config)#banner motd #Authorized Access Only!# Router(config)#hostname R-1 R-1(config)#service password-encryption R-1(config)#interface g0/0/0 R-1(config-if)#ip address 192.168.0.1 255.255.255.0 R-1(config-if)#no shutdown R-1(config-if)#description Link to LAN 1 R-1(config-if)#exit R-1(config)#interface s0/1/0 R-1(config-if)#ip address 209.165.201.2 255.255.255.252 R-1(config-if)#no shutdown R-1(config-if)#description Link to Internet R-1(config-if)#exit
Nota: asegúrese de registrar las contraseñas que cree.
Part 2: Basic Switch Configuration
Step 1: Configure Remote Management Addressing
a. Configure SVI 99 on switch S-3 with IP addressing according to the Addressing Table
b. The S-3 switch SVI should be reachable from other networks.
S-3(config)#interface vlan 99 S-3(config-if)#ip address 192.168.99.18 255.255.255.240 S-3(config-if)#no shutdown S-3(config-if)#exit S-3(config)# S-3(config)#ip default-gateway 192.168.99.17
Step 2: Configure Secure Remote Access
On switch S-3, configure SSH as follows:
– Username: admin password: C1sco123!
– Modulus bits 1024
– All VTY lines should accept SSH connections only
– Connections should require the previously configured username and password.
– IP domain name: acad.pt
S-3(config)#ip domain-name acad.pt
S-3(config)#crypto key generate rsa
How many bits in the modulus [512]: 1024
S-3(config)#username admin privilege 15 secret C1sco123!
S-3(config)#enable secret C1sco123!
S-3(config)#line vty 0 15
S-3(config-line)#transport input ssh
S-3(config-line)#login local
S-3(config-line)#exit
S-3(config)#ip ssh version 2b. Test SSH connectivity to ensure that all necessary settings have been configured. If unable to connect, correct any issues and verify connectivity
Part 3: VLAN Configuration
Step 1: Configure VLANs according to the VLAN table.
Use the VLAN Table to create and name the VLANs on the appropriate switches.
VLAN Table
| VLAN | Name | IP Network | Subnet Mask | Devices |
|---|---|---|---|---|
| 10 | B1F1 | 192.168.10.0 | 255.255.255.0 | MULTI-1, S-1, S-2 |
| 20 | B1F2 | 192.168.20.0 | 255.255.255.0 | MULTI-1, S-1, S-2 |
| 30 | B1F4 | 192.168.30.0 | 255.255.255.0 | MULTI-1, S-1, S-2 |
| 40 | B3 | 192.168.40.0 | 255.255.255.0 | S-3 |
| 50 | B4 | 192.168.50.0 | 255.255.255.0 | S-3 |
| 60 | B5 | 192.168.60.0 | 255.255.255.0 | S-3 |
| 99 | NetAdmin | 192.168.99.16 | 255.255.255.240 | S-3 |
MULTI-1(config)#vlan 10 MULTI-1(config-vlan)#name B1F1 MULTI-1(config-vlan)#interface vlan 10 MULTI-1(config-if)#description B1F1 MULTI-1(config-if)#ip address 192.168.10.1 255.255.255.0 MULTI-1(config-if)#exit MULTI-1(config)# MULTI-1(config)#vlan 20 MULTI-1(config-vlan)#name B1F2 MULTI-1(config-vlan)#interface vlan 20 MULTI-1(config-if)#description B1F2 MULTI-1(config-if)#ip address 192.168.20.1 255.255.255.0 MULTI-1(config-if)#exit MULTI-1(config)# MULTI-1(config)#vlan 30 MULTI-1(config-vlan)#name B1F4 MULTI-1(config-vlan)#interface vlan 30 MULTI-1(config-if)#description B1F4 MULTI-1(config-if)#ip address 192.168.30.1 255.255.255.0 MULTI-1(config-if)#exit MULTI-1(config)# MULTI-1(config)#vlan 99 MULTI-1(config-vlan)#name NetAdmin MULTI-1(config-vlan)#interface vlan 99 MULTI-1(config-if)#description NetAdmin MULTI-1(config-if)#ip address 192.168.99.2 255.255.255.240 MULTI-1(config-if)#exit
S-1(config)#vlan 10 S-1(config-vlan)#name B1F1 S-1(config-vlan)#interface vlan 10 S-1(config-if)#description B1F1 S-1(config-if)#exit S-1(config)# S-1(config)#vlan 20 S-1(config-vlan)#name B1F2 S-1(config-vlan)#interface vlan 20 S-1(config-if)#description B1F2 S-1(config-if)#exit S-1(config)# S-1(config)#vlan 30 S-1(config-vlan)#name B1F4 S-1(config-vlan)#interface vlan 30 S-1(config-if)#description B1F4 S-1(config-if)#exit
S-2(config)#vlan 10 S-2(config-vlan)#name B1F1 S-2(config-vlan)#interface vlan 10 S-2(config-if)#description B1F1 S-2(config-if)#exit S-2(config)# S-2(config)#vlan 20 S-2(config-vlan)#name B1F2 S-2(config-vlan)#interface vlan 20 S-2(config-if)#description B1F2 S-2(config-if)#exit S-2(config)# S-2(config)#vlan 30 S-2(config-vlan)#name B1F4 S-2(config-vlan)#interface vlan 30 S-2(config-if)#description B1F4 S-2(config-if)#exit
S-3(config)#vlan 40 S-3(config-vlan)#name B3 S-3(config-vlan)#interface vlan 40 S-3(config-if)#ip address 192.168.40.1 255.255.255.0 S-3(config-if)#description B3 S-3(config-if)#exit S-3(config)# S-3(config)#vlan 50 S-3(config-vlan)#name B4 S-3(config-vlan)#interface vlan 50 S-3(config-if)#ip address 192.168.50.1 255.255.255.0 S-3(config-if)#description B4 S-3(config-if)#exit S-3(config)# S-3(config)#vlan 60 S-3(config-vlan)#name B5 S-3(config-vlan)#interface vlan 60 S-3(config-if)#ip address 192.168.60.1 255.255.255.0 S-3(config-if)#description B5 S-3(config-if)#exit S-3(config)# S-3(config)#vlan 99 S-3(config-vlan)#name NetAdmin S-3(config-vlan)#interface vlan 99 S-3(config-if)#ip address 192.168.99.18 255.255.255.240 S-3(config-if)#description NetAdmin S-3(config-if)#exit
Step 2: Assign switch ports to VLANs.
Assign VLAN membership to static access switchports according to the Port to VLAN Assignment table.
Port to VLAN Assignment Table
| Device | VLAN | VLAN Name | Port Assignments |
|---|---|---|---|
| S-1 | 10 | B1F1 | F0/7-10 |
| 20 | B1F2 | F0/11-15 | |
| 30 | B1F4 | F0/16-24 | |
| S-2 | 10 | B1F1 | F0/7-10 |
| 20 | B1F2 | F0/11-15 | |
| 30 | B1F4 | F0/16-24 | |
| S-3 | 40 | B3 | F0/1-5 |
| 50 | B4 | F0/6-10 | |
| 60 | B5 | F0/11-15 | |
| 99 | NetAdmin Native | F0/24 |
S-1(config)#interface range f0/7-10 S-1(config-if-range)#switchport mode access S-1(config-if-range)#switchport access vlan 10 S-1(config-if-range)#exit S-1(config)#interface range f0/11-15 S-1(config-if-range)#switchport mode access S-1(config-if-range)#switchport access vlan 20 S-1(config-if-range)#exit S-1(config)#interface range f0/16-24 S-1(config-if-range)#switchport mode access S-1(config-if-range)#switchport access vlan 30 S-1(config-if-range)#exit
S-2(config)#interface range f0/7-10 S-2(config-if-range)#switchport mode access S-2(config-if-range)#switchport access vlan 10 S-2(config-if-range)#exit S-2(config)#interface range f0/11-15 S-2(config-if-range)#switchport mode access S-2(config-if-range)#switchport access vlan 20 S-2(config-if-range)#exit S-2(config)#interface range f0/16-24 S-2(config-if-range)#switchport mode access S-2(config-if-range)#switchport access vlan 30 S-2(config-if-range)#exit
S-3(config)#interface range f0/1-5 S-3(config-if-range)#switchport mode access S-3(config-if-range)#switchport access vlan 40 S-3(config-if-range)#exit S-3(config)#interface range f0/6-10 S-3(config-if-range)#switchport mode access S-3(config-if-range)#switchport access vlan 50 S-3(config-if-range)#exit S-3(config)#interface range f0/11-15 S-3(config-if-range)#switchport mode access S-3(config-if-range)#switchport access vlan 60 S-3(config-if-range)#exit S-3(config)#interface f0/24 S-3(config-if)#switchport mode access S-3(config-if)#switchport access vlan 99 S-3(config-if)#exit
Part 4: EtherChannel and Trunking Configuration
EtherChannel Port Assignments Table
| Channel Group | Devices in Groups | Ports in Group |
|---|---|---|
| 1 | MULTI-1 | G1/0/1, G1/0/2 |
| SW-1 | G0/1, G0/2 | |
| 2 | MULTI-1 | G1/0/3, G1/0/4 |
| SW-2 | G0/1, G0/2 | |
| 3 | SW-1 | F0/5, F0/6 |
| SW-2 | F0/5, F0/6 |
Step 1: Configure EtherChannels
Create EtherChannels according to the EtherChannel Port Assignments Table. Use the Cisco LACP protocol. Both sides of the channel should attempt to negotiate the link protocol.
MULTI-1(config)#interface range g1/0/1-2 MULTI-1(config-if-range)#channel-group 1 mode active MULTI-1(config-if-range)#exit MULTI-1(config)# MULTI-1(config)#interface range g1/0/3-4 MULTI-1(config-if-range)#channel-group 2 mode active MULTI-1(config-if-range)#exit
S-1(config)#interface range g0/1-2 S-1(config-if-range)#channel-group 1 mode active S-1(config-if-range)#exit S-1(config)# S-1(config)#interface range f0/5-6 S-1(config-if-range)#channel-group 3 mode active S-1(config-if-range)#exit
S-2(config)#interface range g0/1-2 S-2(config-if-range)#channel-group 2 mode active S-2(config-if-range)#exit S-2(config)# S-2(config)#interface range f0/5-6 S-2(config-if-range)#channel-group 3 mode active S-2(config-if-range)#exit
Step 2: Configure Trunking on the EtherChannels
a. Configure the port channel interfaces as static trunks. Disable DTP negotiation on all trunks
b. Troubleshoot any issues that prevent the formation of the EtherChannels.
MULTI-1(config)#interface port-channel 1 MULTI-1(config-if)#switchport mode trunk MULTI-1(config-if)#switchport trunk allowed vlan 10,20,30 MULTI-1(config-if)#exit MULTI-1(config)# MULTI-1(config)#interface port-channel 2 MULTI-1(config-if)#switchport mode trunk MULTI-1(config-if)#switchport trunk allowed vlan 10,20,30 MULTI-1(config-if)#exit
S-1(config)#interface port-channel 1 S-1(config-if)#switchport mode trunk S-1(config-if)#switchport nonegotiate S-1(config-if)#exit S-1(config)# S-1(config)#interface port-channel 3 S-1(config-if)#switchport mode trunk S-1(config-if)#switchport nonegotiate S-1(config-if)#exit
S-2(config)#interface port-channel 2 S-2(config-if)#switchport mode trunk S-2(config-if)#switchport nonegotiate S-2(config-if)#exit S-2(config)# S-2(config)#interface port-channel 3 S-2(config-if)#switchport mode trunk S-2(config-if)#switchport nonegotiate S-2(config-if)#exit
Step 3: Configure a static trunk uplink
a. On the S-3 switch, configure the port that is connected to R-1 g0/0/0 as a static trunk
b. Configure the NetAdmin VLAN as the native VLAN
c. Disable DTP on the port.
S-3
S-3(config)#interface g0/1 S-3(config-if)#switchport mode trunk S-3(config-if)#switchport nonegotiate S-3(config-if)#switchport trunk native vlan 99 S-3(config-if)#switchport trunk allowed vlan 40,50,60,99 S-3(config-if)#exit
Part 5: Configure Inter-VLAN Routing
Step 1: Configure inter-VLAN routing on the Layer 3 switch
a. Configure Inter-VLAN routing on the MULTI-1 Layer 3 switch for all VLANs in the VLAN Table that are configured on MULTI-1.
b. Configure the switchport on MULTI-1 that is connected to R-1 with an IP address as shown in the Addressing Table.
MULTI-1(config)#ip routing MULTI-1(config)#interface g1/1/1 MULTI-1(config-if)#no switchport MULTI-1(config-if)#ip address 192.168.0.2 255.255.255.0
Step 2: Configure router-on-a-stick inter-VLAN routing on a router.
a. Configure inter-VLAN routing on R-1 for all the VLANs that are configured on the S-3 switch. Use the information in the Addressing Table
b. Be sure to configure descriptions of all interfaces
R-1
R-1(config)#interface g0/0/1 R-1(config-if)#no shutdown R-1(config)#interface g0/0/1.40 R-1(config-subif)#description "Gateway for VLAN40" R-1(config-subif)#encapsulation dot1q 40 R-1(config-subif)#ip address 192.168.40.1 255.255.255.0 R-1(config-subif)#exit R-1(config)#interface g0/0/1.50 R-1(config-subif)#description "Gateway for VLAN50" R-1(config-subif)#encapsulation dot1q 50 R-1(config-subif)#ip address 192.168.50.1 255.255.255.0 R-1(config-subif)#exit R-1(config)#interface g0/0/1.60 R-1(config-subif)#description "Gateway for VLAN60" R-1(config-subif)#encapsulation dot1q 60 R-1(config-subif)#ip address 192.168.60.1 255.255.255.0 R-1(config-subif)#exit R-1(config)#interface g0/0/1.99 R-1(config-subif)#description "Gateway for VLAN99" R-1(config-subif)#encapsulation dot1q 99 native R-1(config-subif)#ip address 192.168.99.17 255.255.255.240 R-1(config-subif)#exit
Step 3: Configure default gateways on hosts.
a Configure default gateway addresses on all hosts on the LANs.
Default gateway on PC1 and PC4: 192.168.10.1
Default gateway on PC2 and PC5: 192.168.20.1
Default gateway on PC3 and PC6: 192.168.30.1
Default gateway on PC7: 192.168.40.1
Default gateway on PC8: 192.168.50.1
Default gateway on PC9: 192.168.60.1
Default gateway on PC99: 192.168.99.17
b. Verify connectivity between all hosts on both LANs with each other and the Web Server server
c. Verify that a host can connect to the SVI of switch S-2 over SSH.
Intructions – Answers
Router RTR-1; R-1; Edge-Router
en conf t ip route 192.168.10.0 255.255.255.0 GigabitEthernet0/0/0 ip route 192.168.20.0 255.255.255.0 GigabitEthernet0/0/0 ip route 192.168.30.0 255.255.255.0 GigabitEthernet0/0/0 ip route 192.168.99.0 255.255.255.240 GigabitEthernet0/0/0 no ip domain lookup enable secret class line console 0 password cisco login exit line vty 0 4 password cisco login exit banner motd #Authorized Access Only!# hostname R-1 service password-encryption interface g0/0/0 ip address 192.168.0.1 255.255.255.0 no shutdown description "R1 G0/0/0" exit interface s0/1/0 ip address 209.165.201.2 255.255.255.252 no shutdown description "R1 S0/1/0" exit interface g0/0/1 no shutdown interface g0/0/1.40 description "Gateway for VLAN40" encapsulation dot1q 40 ip address 192.168.40.1 255.255.255.0 exit interface g0/0/1.50 description "Gateway for VLAN50" encapsulation dot1q 50 ip address 192.168.50.1 255.255.255.0 exit interface g0/0/1.60 description "Gateway for VLAN60" encapsulation dot1q 60 ip address 192.168.60.1 255.255.255.0 exit interface g0/0/1.99 description "Gateway for VLAN99" encapsulation dot1q 99 native ip address 192.168.99.17 255.255.255.240 end copy running-config startup-config
Switch S-3 ; SW-3; Sw-C
en config t interface vlan 99 ip address 192.168.99.18 255.255.255.240 no shutdown exit ip default-gateway 192.168.99.17 ip domain-name acad.pt crypto key generate rsa 1024 username admin privilege 15 secret C1sco123! enable secret C1sco123! line vty 0 15 transport input ssh login local exit ip ssh version 2 vlan 40 name B3 exit interface vlan 40 ip address 192.168.40.1 255.255.255.0 description B3 exit vlan 50 name B4 exit interface vlan 50 ip address 192.168.50.1 255.255.255.0 description B4 exit vlan 60 name B5 exit interface vlan 60 ip address 192.168.60.1 255.255.255.0 description B5 exit vlan 99 name NetAdmin exit interface vlan 99 ip address 192.168.99.18 255.255.255.240 description NetAdmin exit interface range f0/1-5 switchport mode access switchport access vlan 40 exit interface range f0/6-10 switchport mode access switchport access vlan 50 exit interface range f0/11-15 switchport mode access switchport access vlan 60 exit interface f0/24 switchport mode access switchport access vlan 99 exit interface g0/1 switchport mode trunk switchport nonegotiate switchport trunk allowed vlan 40,50,60,99 switchport trunk native vlan 99 end copy running-config startup-config
Switch MULTI-1; MSW-1; L3-SW1
en config t vlan 10 name B1F1 interface vlan 10 description B1F1 ip address 192.168.10.1 255.255.255.0 exit vlan 20 name B1F2 interface vlan 20 description B1F2 ip address 192.168.20.1 255.255.255.0 exit vlan 30 name B1F4 interface vlan 30 description B1F4 ip address 192.168.30.1 255.255.255.0 exit vlan 99 name NetAdmin interface vlan 99 description NetAdmin ip address 192.168.99.2 255.255.255.240 exit ip routing interface g1/1/1 no switchport ip address 192.168.0.2 255.255.255.0 exit interface range g1/0/1-2 channel-group 1 mode active exit interface port-channel 1 switchport mode trunk switchport trunk allowed vlan 10,20,30 exit interface range g1/0/3-4 channel-group 2 mode active exit interface port-channel 2 switchport mode trunk switchport trunk allowed vlan 10,20,30 end copy running-config startup-config
Switch S-1; SW-1; Sw-A
enable config terminal vlan 10 name B1F1 interface vlan 10 description B1F1 exit vlan 20 name B1F2 interface vlan 20 description B1F2 exit vlan 30 name B1F4 interface vlan 30 description B1F4 exit interface range f0/7-10 switchport mode access switchport access vlan 10 exit interface range f0/11-15 switchport mode access switchport access vlan 20 exit interface range f0/16-24 switchport mode access switchport access vlan 30 exit interface range g0/1-2 channel-group 1 mode active exit interface port-channel 1 switchport mode trunk switchport nonegotiate exit interface range f0/5-6 channel-group 3 mode active exit interface port-channel 3 switchport mode trunk switchport nonegotiate end copy running-config startup-config
Switch S-2; SW-2; Sw-B
en config t vlan 10 name B1F1 interface vlan 10 description B1F1 exit vlan 20 name B1F2 interface vlan 20 description B1F2 exit vlan 30 name B1F4 interface vlan 30 description B1F4 exit interface range f0/7-10 switchport mode access switchport access vlan 10 exit interface range f0/11-15 switchport mode access switchport access vlan 20 exit interface range f0/16-24 switchport mode access switchport access vlan 30 exit interface range g0/1-2 channel-group 2 mode active exit interface port-channel 2 switchport mode trunk switchport nonegotiate exit interface range f0/5-6 channel-group 3 mode active exit interface port-channel 3 switchport mode trunk switchport nonegotiate end copy running-config startup-config
Configure default gateway addresses on all hosts on the LANs.
Default gateway on Host1 and Host4: 192.168.10.1
Default gateway on Host2 and Host5: 192.168.20.1
Default gateway on Host3 and Host6: 192.168.30.1
Default gateway on Host7: 192.168.40.1
Default gateway on Host8: 192.168.50.1
Default gateway on Host9: 192.168.60.1
Default gateway on Host99: 192.168.99.17
Download PDF and Packet Tracer files:
Type 2 – 172.31
A few things to keep in mind while completing this activity:
- 1. Do not use the browser Back button or close or reload any exam windows during the exam.
- 2. Do not close Packet Tracer when you are done. It will close automatically.
- 3. Click the Submit Assessment button in the browser window to submit your work.
Introduction
In this assessment you are configuring a network that is using EtherChannel and routing between VLANs. For the sake of time, you will not be asked to perform all configurations on all network devices as you may be required to do in a real network or other assessment. Instead, you will use the skills and knowledge that you have learned in the labs in this course to configure the router and switches in the topology. In addition to EtherChannel and inter-VLAN routing, this task involves creating VLANs and trunks, and performing basic router and switch configuration.
You are required to configure host default gateways; however host addresses are preconfigured.
You will practice and be assessed on the following skills:
- Configuration of initial settings on a router.
- Configuration of initial settings on a switch, including SVI and SSH.
- Configuration of VLANs.
- Configuration of switchport VLAN membership.
- EtherChannel configuration.
- Troubleshooting VLANs.
- Configuration of static trunking and DTP.
- Configuration of routing between VLANs on a Layer 3 switch.
- Configuration of router-on-a-stick inter- VLAN routing on a router.
- Configure default gateways on hosts.
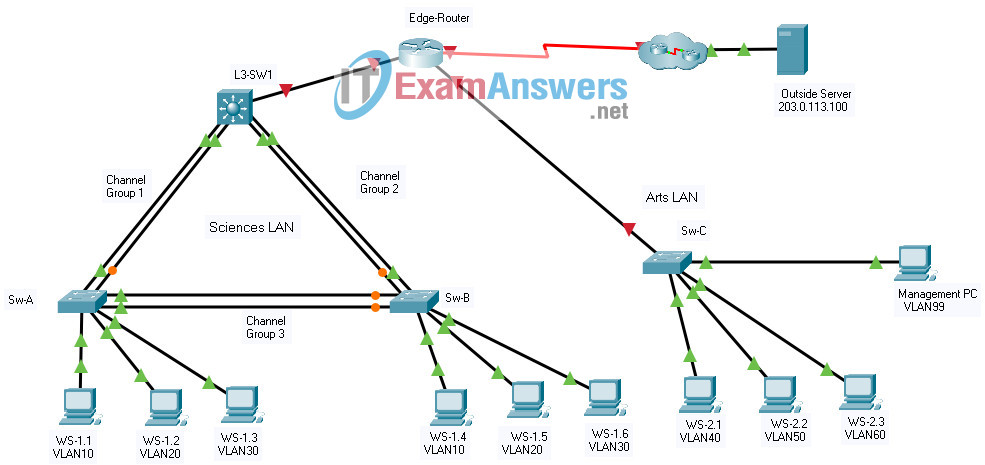
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| Edge-Router | G0/0/0 | 172.31.0.1 | 255.255.255.0 |
| G0/0/1.40 | 172.31.40.1 | 255.255.255.0 | |
| G0/0/1.50 | 172.31.50.1 | 255.255.255.0 | |
| G0/0/1.60 | 172.31.60.1 | 255.255.255.0 | |
| G0/0/1.99 | 172.31.99.17 | 255.255.255.240 | |
| S0/1/0 | 209.165.201.2 | 255.255.255.252 | |
| L3-SW1 | G1/1/1 | 172.31.0.2 | 255.255.255.0 |
| VLAN10 | 172.31.10.1 | 255.255.255.0 | |
| VLAN20 | 172.31.20.1 | 255.255.255.0 | |
| VLAN30 | 172.31.30.1 | 255.255.255.0 | |
| VLAN99 | 172.31.99.2 | 255.255.255.240 | |
| Sw-C | VLAN99 | 172.31.99.18 | 255.255.255.240 |
| WS-1.1 | NIC | 172.31.10.10 | 255.255.255.0 |
| WS-1.2 | NIC | 172.31.20.20 | 255.255.255.0 |
| WS-1.3 | NIC | 172.31.30.30 | 255.255.255.0 |
| WS-1.4 | NIC | 172.31.10.11 | 255.255.255.0 |
| WS-1.5 | NIC | 172.31.20.21 | 255.255.255.0 |
| WS-1.6 | NIC | 172.31.30.31 | 255.255.255.0 |
| WS-2.1 | NIC | 172.31.40.40 | 255.255.255.0 |
| WS-2.2 | NIC | 172.31.50.50 | 255.255.255.0 |
| WS-2.3 | NIC | 172.31.60.60 | 255.255.255.0 |
| Management PC | NIC | 172.31.99.19 | 255.255.255.0 |
| Outside Server | NIC | 203.0.113.100 | 255.255.255.0 |
Background / Scenario
A corporation is planning to implement EtherChannel and a new VLAN design in order to make the network more efficient. You have been asked to work on a design and prototype of the new network. You have created the logical topology and now need to configure the devices in order to evaluate the design. You will configure VLANs and access port VLAN membership on access layer switches. You will also configure EtherChannel and trunking. Finally, you will configure a router and a Layer 3 switch to route between VLANs. Some addressing had already been configured.
Instructions
Part 1: Basic Router Configuration
Step 1: Configure router Edge-Router with required settings.
a. Open a command window on router Edge-Router and move to privileged EXEC mode
b. Copy and paste the following configuration into the Edge-Router router CLI.
Router(config)#ip route 172.31.10.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 172.31.20.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 172.31.30.0 255.255.255.0 GigabitEthernet0/0/0 Router(config)#ip route 172.31.99.0 255.255.255.240 GigabitEthernet0/0/0
Be sure to press the Enter key after the last line to return to privileged EXEC mode prompt.
c. Configure the following settings on the router
– The enable secret password.
– A console password
– Remote access to the VTY lines.
– A banner MOTD message.
– The device hostname according to the value in the addressing table.
– All clear text passwords should be encrypted.
– Interface addressing on g0/0/0 and s0/1/0
– Interface descriptions on g0/0/0 and s0/1/0.
Router(config)#no ip domain lookup Router(config)#enable secret class Router(config)#line console 0 Router(config-line)#password cisco Router(config-line)#login Router(config-line)#exit Router(config)#line vty 0 4 Router(config-line)#password cisco Router(config-line)#login Router(config-line)#exit Router(config)#banner motd #Authorized Access Only!# Router(config)#hostname Edge-Router Edge-Router(config)#service password-encryption Edge-Router(config)#interface g0/0/0 Edge-Router(config-if)#ip address 172.31.0.1 255.255.255.0 Edge-Router(config-if)#no shutdown Edge-Router(config-if)#description Link to LAN 1 Edge-Router(config-if)#exit Edge-Router(config)#interface s0/1/0 Edge-Router(config-if)#ip address 209.165.201.2 255.255.255.252 Edge-Router(config-if)#no shutdown Edge-Router(config-if)#description Link to Internet Edge-Router(config-if)#exit
Note: Be sure to make a record of the passwords that you create.
Part 2: Basic Switch Configuration
Step 1: Configure Remote Management Addressing
a. Configure SVI 99 on switch Sw-C with IP addressing according to the Addressing Table
b. The Sw-C switch SVI should be reachable from other networks.
Sw-C(config)#interface vlan 99 Sw-C(config-if)#ip address 172.31.99.18 255.255.255.240 Sw-C(config-if)#no shutdown Sw-C(config-if)#exit Sw-C(config)# Sw-C(config)#ip default-gateway 172.31.99.17
Step 2: Configure Secure Remote Access
On switch Sw-C, configure SSH as follows:
– Username: admin password: C1sco123!
– Modulus bits 1024
– All VTY lines should accept SSH connections only
– Connections should require the previously configured username and password.
– IP domain name: acad.pt
Sw-C(config)#ip domain-name acad.pt
Sw-C(config)#crypto key generate rsa
How many bits in the modulus [512]: 1024
Sw-C(config)#username admin privilege 15 secret C1sco123!
Sw-C(config)#enable secret C1sco123!
Sw-C(config)#line vty 0 15
Sw-C(config-line)#transport input ssh
Sw-C(config-line)#login local
Sw-C(config-line)#exit
Sw-C(config)#ip ssh version 2
b. Test SSH connectivity to ensure that all necessary settings have been configured. If unable to connect, correct any issues and verify connectivity
Part 3: VLAN Configuration
Step 1: Configure VLANs according to the VLAN table.
Use the VLAN Table to create and name the VLANs on the appropriate switches.
VLAN Table
| VLAN | Name | IP Network | Subnet Mask | Devices |
|---|---|---|---|---|
| 10 | B1F1 | 172.31.10.0 | 255.255.255.0 | L3-SW1, Sw-A, Sw-B |
| 20 | B1F2 | 172.31.20.0 | 255.255.255.0 | L3-SW1, Sw-A, Sw-B |
| 30 | B1F4 | 172.31.30.0 | 255.255.255.0 | L3-SW1, Sw-A, Sw-B |
| 40 | B3 | 172.31.40.0 | 255.255.255.0 | Sw-C |
| 50 | B4 | 172.31.50.0 | 255.255.255.0 | Sw-C |
| 60 | B5 | 172.31.60.0 | 255.255.255.0 | Sw-C |
| 99 | NetAdmin | 172.31.99.16 | 255.255.255.240 | Sw-C, L3-SW1 |
L3-SW1
L3-SW1(config)#vlan 10 L3-SW1(config-vlan)#name B1F1 L3-SW1(config-vlan)#interface vlan 10 L3-SW1(config-if)#description B1F1 L3-SW1(config-if)#ip address 172.31.10.1 255.255.255.0 L3-SW1(config-if)#exit L3-SW1(config)# L3-SW1(config)#vlan 20 L3-SW1(config-vlan)#name B1F2 L3-SW1(config-vlan)#interface vlan 20 L3-SW1(config-if)#description B1F2 L3-SW1(config-if)#ip address 172.31.20.1 255.255.255.0 L3-SW1(config-if)#exit L3-SW1(config)# L3-SW1(config)#vlan 30 L3-SW1(config-vlan)#name B1F4 L3-SW1(config-vlan)#interface vlan 30 L3-SW1(config-if)#description B1F4 L3-SW1(config-if)#ip address 172.31.30.1 255.255.255.0 L3-SW1(config-if)#exit L3-SW1(config)# L3-SW1(config)#vlan 99 L3-SW1(config-vlan)#name NetAdmin L3-SW1(config-vlan)#interface vlan 99 L3-SW1(config-if)#description NetAdmin L3-SW1(config-if)#ip address 172.31.99.2 255.255.255.240 L3-SW1(config-if)#exit
Step 2: Assign switch ports to VLANs.
Assign VLAN membership to static access switchports according to the Port to VLAN Assignment table.
Port to VLAN Assignment Table
| Device | VLAN | VLAN Name | Port Assignments |
|---|---|---|---|
| Sw-A | 10 | B1F1 | F0/7-10 |
| 20 | B1F2 | F0/11-15 | |
| 30 | B1F4 | F0/16-24 | |
| Sw-B | 10 | B1F1 | F0/7-10 |
| 20 | B1F2 | F0/11-15 | |
| 30 | B1F4 | F0/16-24 | |
| Sw-C | 40 | B3 | F0/1-5 |
| 50 | B4 | F0/6-10 | |
| 60 | B5 | F0/11-15 | |
| 99 | NetAdmin Native | F0/24 |
Sw-A
Sw-A(config)#interface range f0/7-10 Sw-A(config-if-range)#switchport mode access Sw-A(config-if-range)#switchport access vlan 10 Sw-A(config-if-range)#exit Sw-A(config)#interface range f0/11-15 Sw-A(config-if-range)#switchport mode access Sw-A(config-if-range)#switchport access vlan 20 Sw-A(config-if-range)#exit Sw-A(config)#interface range f0/16-24 Sw-A(config-if-range)#switchport mode access Sw-A(config-if-range)#switchport access vlan 30 Sw-A(config-if-range)#exit
Part 4: EtherChannel and Trunking Configuration
EtherChannel Port Assignments Table
| Channel Group | Devices in Groups | Ports in Group |
|---|---|---|
| 1 | L3-SW1 | G1/0/1, G1/0/2 |
| Sw-A | G0/1, G0/2 | |
| 2 | L3-SW1 | G1/0/3, G1/0/4 |
| Sw-B | G0/1, G0/2 | |
| 3 | Sw-A | F0/5, F0/6 |
| Sw-B | F0/5, F0/6 |
Step 1: Configure EtherChannels
Create EtherChannels according to the EtherChannel Port Assignments Table. Use the Cisco LACP protocol. Both sides of the channel should attempt to negotiate the link protocol.
L3-SW1
L3-SW1(config)#interface range g1/0/1-2 L3-SW1(config-if-range)#channel-group 1 mode active L3-SW1(config-if-range)#exit L3-SW1(config)# L3-SW1(config)#interface range g1/0/3-4 L3-SW1(config-if-range)#channel-group 2 mode active L3-SW1(config-if-range)#exit
Step 2: Configure Trunking on the EtherChannels
a. Configure the port channel interfaces as static trunks. Disable DTP negotiation on all trunks
b. Troubleshoot any issues that prevent the formation of the EtherChannels.
L3-SW1
L3-SW1(config)#interface port-channel 1 L3-SW1(config-if)#switchport mode trunk L3-SW1(config-if)#switchport trunk allowed vlan 10,20,30 L3-SW1(config-if)#exit L3-SW1(config)# L3-SW1(config)#interface port-channel 2 L3-SW1(config-if)#switchport mode trunk L3-SW1(config-if)#switchport trunk allowed vlan 10,20,30 L3-SW1(config-if)#exit
Note: Packet Tracer requires configuration of trunking and DTP mode on both portchannel interfaces and the component physical interfaces.
Step 3: Configure a static trunk uplink
a. On the Sw-C switch, configure the port that is connected to Edge-Router g0/0/0 as a static trunk
b. Configure the NetAdmin VLAN as the native VLAN
c. Disable DTP on the port.
Sw-C
Sw-C(config)#interface g0/1 Sw-C(config-if)#switchport mode trunk Sw-C(config-if)#switchport nonegotiate Sw-C(config-if)#switchport trunk native vlan 99 Sw-C(config-if)#switchport trunk allowed vlan 40,50,60,99 Sw-C(config-if)#exit
Part 5: Configure Inter-VLAN Routing
Step 1: Configure inter-VLAN routing on the Layer 3 switch
a. Configure Inter-VLAN routing on the L3-SW1 Layer 3 switch for all VLANs in the VLAN Table that are configured on L3-SW1.
b. Configure the switchport on L3-SW1 that is connected to Edge-Router with an IP address as shown in the Addressing Table.
L3-SW1(config)#ip routing L3-SW1(config)#interface g1/1/1 L3-SW1(config-if)#no switchport L3-SW1(config-if)#ip address 172.31.0.2 255.255.255.0
Step 2: Configure router-on-a-stick inter-VLAN routing on a router.
a. Configure inter-VLAN routing on Edge-Router for all the VLANs that are configured on the Sw-C switch. Use the information in the Addressing Table
b. Be sure to configure descriptions of all interfaces
Edge-Router
Edge-Router(config)#interface g0/0/1 Edge-Router(config-if)#no shutdown Edge-Router(config)#interface g0/0/1.40 Edge-Router(config-subif)#description "Gateway for VLAN40" Edge-Router(config-subif)#encapsulation dot1q 40 Edge-Router(config-subif)#ip address 172.31.40.1 255.255.255.0 Edge-Router(config-subif)#exit Edge-Router(config)#interface g0/0/1.50 Edge-Router(config-subif)#description "Gateway for VLAN50" Edge-Router(config-subif)#encapsulation dot1q 50 Edge-Router(config-subif)#ip address 172.31.50.1 255.255.255.0 Edge-Router(config-subif)#exit Edge-Router(config)#interface g0/0/1.60 Edge-Router(config-subif)#description "Gateway for VLAN60" Edge-Router(config-subif)#encapsulation dot1q 60 Edge-Router(config-subif)#ip address 172.31.60.1 255.255.255.0 Edge-Router(config-subif)#exit Edge-Router(config)#interface g0/0/1.99 Edge-Router(config-subif)#description "Gateway for VLAN99" Edge-Router(config-subif)#encapsulation dot1q 99 native Edge-Router(config-subif)#ip address 172.31.99.17 255.255.255.240 Edge-Router(config-subif)#exit
Step 3: Configure default gateways on hosts.
a Configure default gateway addresses on all hosts on the LANs.
Default gateway on PC1 and PC4: 172.31.10.1
Default gateway on PC2 and PC5: 172.31.20.1
Default gateway on PC3 and PC6: 172.31.30.1
Default gateway on PC7: 172.31.40.1
Default gateway on PC8: 172.31.50.1
Default gateway on PC9: 172.31.60.1
Default gateway on PC99: 172.31.99.17
b. Verify connectivity between all hosts on both LANs with each other and the Web Server server
c. Verify that a host can connect to the SVI of switch Sw-B over SSH.
Intructions – Answers

Router Edge-Router
en conf t ip route 172.31.10.0 255.255.255.0 GigabitEthernet0/0/0 ip route 172.31.20.0 255.255.255.0 GigabitEthernet0/0/0 ip route 172.31.30.0 255.255.255.0 GigabitEthernet0/0/0 ip route 172.31.99.0 255.255.255.240 GigabitEthernet0/0/0 no ip domain lookup enable secret class line console 0 password cisco login exit line vty 0 4 password cisco login exit banner motd #Authorized Access Only!# hostname Edge-Router service password-encryption interface g0/0/0 ip address 172.31.0.1 255.255.255.0 no shutdown description "R1 G0/0/0" exit interface s0/1/0 ip address 209.165.201.2 255.255.255.252 no shutdown description "R1 S0/1/0" exit interface g0/0/1 no shutdown interface g0/0/1.40 description "Gateway for VLAN40" encapsulation dot1q 40 ip address 172.31.40.1 255.255.255.0 exit interface g0/0/1.50 description "Gateway for VLAN50" encapsulation dot1q 50 ip address 172.31.50.1 255.255.255.0 exit interface g0/0/1.60 description "Gateway for VLAN60" encapsulation dot1q 60 ip address 172.31.60.1 255.255.255.0 exit interface g0/0/1.99 description "Gateway for VLAN99" encapsulation dot1q 99 native ip address 172.31.99.17 255.255.255.240 end copy running-config startup-config
Switch Sw-C or SW-3
en config t interface vlan 99 ip address 172.31.99.18 255.255.255.240 no shutdown exit ip default-gateway 172.31.99.17 ip domain-name acad.pt crypto key generate rsa 1024 username admin privilege 15 secret C1sco123! enable secret C1sco123! line vty 0 15 transport input ssh login local exit ip ssh version 2 vlan 40 name B3 exit interface vlan 40 ip address 172.31.40.1 255.255.255.0 description B3 exit vlan 50 name B4 exit interface vlan 50 ip address 172.31.50.1 255.255.255.0 description B4 exit vlan 60 name B5 exit interface vlan 60 ip address 172.31.60.1 255.255.255.0 description B5 exit vlan 99 name NetAdmin exit interface vlan 99 ip address 172.31.99.18 255.255.255.240 description NetAdmin exit interface range f0/1-5 switchport mode access switchport access vlan 40 exit interface range f0/6-10 switchport mode access switchport access vlan 50 exit interface range f0/11-15 switchport mode access switchport access vlan 60 exit interface f0/24 switchport mode access switchport access vlan 99 exit interface g0/1 switchport mode trunk switchport nonegotiate switchport trunk allowed vlan 40,50,60,99 switchport trunk native vlan 99 end copy running-config startup-config
Switch L3-SW1 or MSw-A
en config t vlan 10 name B1F1 interface vlan 10 description B1F1 ip address 172.31.10.1 255.255.255.0 exit vlan 20 name B1F2 interface vlan 20 description B1F2 ip address 172.31.20.1 255.255.255.0 exit vlan 30 name B1F4 interface vlan 30 description B1F4 ip address 172.31.30.1 255.255.255.0 exit vlan 99 name NetAdmin interface vlan 99 description NetAdmin ip address 172.31.99.2 255.255.255.240 exit ip routing interface g1/1/1 no switchport ip address 172.31.0.2 255.255.255.0 exit interface range g1/0/1-2 channel-group 1 mode active exit interface port-channel 1 switchport mode trunk switchport trunk allowed vlan 10,20,30 exit interface range g1/0/3-4 channel-group 2 mode active exit interface port-channel 2 switchport mode trunk switchport trunk allowed vlan 10,20,30 end copy running-config startup-config
Switch Sw-A
enable config terminal vlan 10 name B1F1 interface vlan 10 description B1F1 exit vlan 20 name B1F2 interface vlan 20 description B1F2 exit vlan 30 name B1F4 interface vlan 30 description B1F4 exit interface range f0/7-10 switchport mode access switchport access vlan 10 exit interface range f0/11-15 switchport mode access switchport access vlan 20 exit interface range f0/16-24 switchport mode access switchport access vlan 30 exit interface range g0/1-2 channel-group 1 mode active exit interface port-channel 1 switchport mode trunk switchport nonegotiate exit interface range f0/5-6 channel-group 3 mode active exit interface port-channel 3 switchport mode trunk switchport nonegotiate end copy running-config startup-config
Switch Sw-B
en config t vlan 10 name B1F1 interface vlan 10 description B1F1 exit vlan 20 name B1F2 interface vlan 20 description B1F2 exit vlan 30 name B1F4 interface vlan 30 description B1F4 exit interface range f0/7-10 switchport mode access switchport access vlan 10 exit interface range f0/11-15 switchport mode access switchport access vlan 20 exit interface range f0/16-24 switchport mode access switchport access vlan 30 exit interface range g0/1-2 channel-group 2 mode active exit interface port-channel 2 switchport mode trunk switchport nonegotiate exit interface range f0/5-6 channel-group 3 mode active exit interface port-channel 3 switchport mode trunk switchport nonegotiate end copy running-config startup-config
Configure default gateway addresses on all hosts on the LANs.
Default gateway on Host1 and Host4: 172.31.10.1
Default gateway on Host2 and Host5: 172.31.20.1
Default gateway on Host3 and Host6: 172.31.30.1
Default gateway on Host7: 172.31.40.1
Default gateway on Host8: 172.31.50.1
Default gateway on Host9: 172.31.60.1
Default gateway on Host99: 172.31.99.17